
FAQs
Below is a small selection of frequently asked questions from our users. If there is something you’d like to ask us that is not on the list please get in touch using our Contact Page
Account
How do I get started with VPNTunnel?
Purchase
Start by choosing the package that suits you best (you can find more information on our packages, below), and choosing how many months you want it to run.
Once you have made the payment, you will receive a welcome email with your log in details for VPNtunnel. Don’t forget to set your inbox filter to allow emails from VPNtunnel!
Login
Log in using the control panel at the top right corner of our homepage. There, you will find guides to help you get started using VPNtunnel
Connect
Use your log in details to connect to your VPN tunnel and you will be on your way in no time.
How can I change or extend my account?
You can see how many days your account will be active for in the control panel. If you want, you can extend this time.
All you have to do is choose how many days you want to extend your account for, and a page from our payment partner will open up, allowing you to make a secure payment.
Upgrade
You always have the option to upgrade or downgrade your account on our control panel.
VPN Technology
What operating systems do you support?
We support all the usual operating systems
PPTP – Windows, Mac, Linux, iOS, Android
OpenVPN – Windows, Mac, Linux
You can use your account wherever you are
You can use your account with VPNtunnel wherever you are. At work, at home, or when traveling
Your account is not locked to a device
You can connect various devices to your VPN tunnel. The only limitation is that you can only have one device connected at a time. To have more than one device connected at the same time, you will need a corresponding number of accounts
Will I really remain anonymous?
You will be assigned an anonymous IP address
VPNtunnel can hide IP addresses by swapping your IP address with a new one that belongs to us. This means that your digital footprints cannot be connected to you as a physical person.
We store no traffic logs
We offer anonymous surfing and our policy is to safeguard our users’ privacy. The only details we save are your username and email address. This means that we never log IP addresses, times or any other details like that. This is always valid for our servers in Sweden. Have a look at our Privacy Policy/TOS to see the specific terms for other countries.
Your traffic remains anonymous, even to your internet service provider or employer
As we encrypt all your traffic, in principle it is impossible for either your internet service provider or employer to see what you are doing on the internet. I.e. they cannot see what websites you have visited, and so on.
We cannot give out information to third parties
As regards our servers in Sweden and other countries where we keep no traffic logs, it is impossible to provide details that can, for example, connect a specific user to a specific activity at a specific time for the simple reason that we do not store this data. In other words, it is not an issue we have to consider anytime such a request is made. For countries where logs have to be kept, we will only ever provide information when legally required to do.
What is VPN?
VPN (Virtual Private Network) is a network to which you connect from your pc, mobile device etc. To connect you usually use third party software such as OpenVPN which is easy to install and configure. Once connected to a VPN network your communication with the world goes through it and not through the usual network routes of your Internet service provider.
Multiple physical and logical networks
Essentially, a VPN is called virtual network because it may span over multiple physical and logical networks to form a single, restricted virtual network on top of them. Thanks to this abstract and virtual design, VPN users don’t have to be geographically limited to a single location but may spread anywhere with access to Internet. The need for such virtual networks is very high in today’s global world where companies and organization have offices in various geographical locations and users may be spread all over the world. The only way for such emote users to be integrated in the work process, i.e. to connect to internal resources, file shares, printers, etc, is through the use of VPN connectivity.
External connectivity
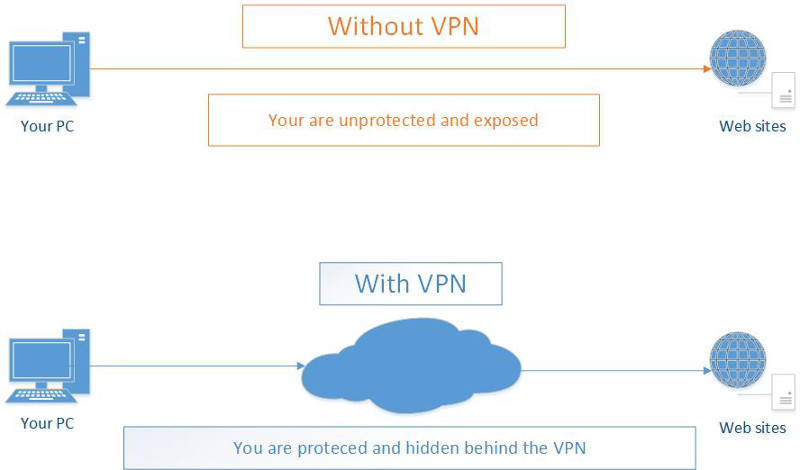
Furthermore, another strong feature of VPNs is their external connectivity. VPNs allow remote. Once you are connected to a VPN, you are able to access outside resources, such as external web sites, through the VPN gateway. VPN’s unmatched support for external connectivity and browsing is very useful to privacy and security. When you connect to sites and Internet resources through a VPN your actual location and identity remain hidden. There is no feasible way for anyone, from aggressive marketing companies to repressing governments, to follow your activity. To anyone trying to interfere with your privacy you will be just another anonymous VPN user who has no location, nor identity. This makes VPNs indispensable to anyone concerned with his privacy – from the average home user who refuses to be under marketing surveillance to human right fighters living in dictatorships.
The external connectivity of VPNs can be also used for accessing restricted sites. For example, when a government has blocked a site, such as in China, VPNs not only allow you to access such blocked sites but they also hide your identity, protecting you from complications with local authorities. In other cases, companies restrict the use of their sites and the features they offer only to users within certain geographical regions. VPNs allow to avoid any such usually unjustified restrictions and still get full access to geographically limited sites.
Online security
Except the fact that VPNs protect your identity, they are also of great value to your online security, especially when transmitting sensible information online. This is due to the fact that once you are connected to a VPN, all your traffic becomes encrypted and impossible to be read and understood. Thus, even if your communication is eavesdropped no one will be able to decipher what site you are connecting to, nor what information you are exchanging online. That’s why traffic encryption is essential when you make online payments and use credit cards or when you just have private communications with third parties. Thus, thanks to VPN’s encryption your sensible data will remain protected even if you are connected to insecure networks such as public Wifis.
All security and privacy features of the VPN technology make it a necessity in today’s age of increasingly insecure communications, security breaches and privacy crimes. Whether you are a human rights fighter or just sensible online user, VPNs is your only choice to protecting yourself and the people you are communicating with.
How to choose a VPN provider
Once you are convinced that you need VPN, then you should carefully choose your VPN provider. There are three essential tips on choosing the best VPN provider for you. First is the ease of use of the software and its support. You’d definitely want to avoid complex, unreliable software which messes up your computer and takes you too much time to configure. Next, you should make sure your VPN provider supports strong encryption to protect your communication. Not all providers are able to offer such strong encryption because it requires more resources. Finally, ensure that your VPN provider has enough points of presence and gateways with fast connectivity, especially in geographic location you are interested. All of these requirements are perfectly satisfied by vpntunnel.com to ensure your excellent experience and protection.
What is OpenVPN and how can I use it?
OpenVPN is one of the most popular and widely used VPN software solutions. Its popularity is due to its strong features, ease of use and extensive support.
OpenVPN is Open Source software which means that everyone can freely use it and modify it as needed. OpenVPN can be used for various connectivity needs but its especially popular for anonymous and private access to Internet.
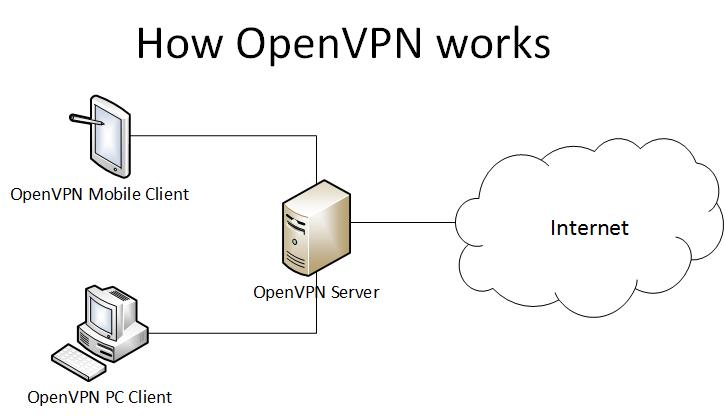
OpenVPN works in client – server mode. This means that there is an OpenVPN server which is connected to the Internet. OpenVPN clients connect to the server and from there they have full access to Internet.
Once connected to the server, the client uses the server to terminate all of its Internet traffic. This means that the client is seen as the server, i.e. the client assumes the physical location and administrative contacts of the server. Thus all the privacy of the OpenVPN client is protected.
How OpenVPN works
In order to start using OpenVPN you need first an OpenVPN server to which to connect to. You could install an OpenVPN server by yourself but this requires some technical knowledge and it lacks many of the privacy features provided by leading VPN service providers. That’s why it’s recommended to use a proven service provider such as VPNTunnel.com.
How to choose OpenVPN provider
While there are many service providers, the benefits of using VPNTunnel.com are:
- More than 25 physical locations all over North and South America, Europe, Asia and Australia: Argentina, Australia, Canada, France, Germany, Great Britain, Iceland, Italy, Luxembourg, Netherlands, Panama, Russia, Singapore, Spain, Sweden, Switzerland, Turkey, USA. This ensures that you will be able to connect from and to virtually everywhere in the world. Thus no site will be blocking you any longer based on your geographical location and the latter remains always undisclosed. No other OpenVPN service provider offers so many locations at the bandwidth and price of VPNTunnel.com.
- Extensive support for a wide array of hardware. Virtually you can use any piece of hardware, including PCs, laptops and mobile devices, which supports OpenVPN.
- Strong privacy protection. VPNTunnel.com is government safe and no traffic data or logs are saved. This means that no one will be able to find any personal details of the users. This unmatched level of protection is unique to VPNTunnel.com and no other company is so dedicated.
- Strong encryption and security protection. Thanks to the strong, enterprise-grade encryption (BF-CBC) provided by VPNTunnel.com your data traffic cannot be intercepted by third parties. This makes it perfectly safe to use any network from public WiFis to monitored networks in repressed countries.
The above key benefits of VPNTunnel.com make it the best choice for OpenVPN service provider at an affordable price with flexible billing cycles.
How to use OpenVPN
Once you have subscribed to an OpenVPN provider you can proceed with the client setup. With VPNTunnel.com the client setup is very easy and straightforward. Here is how to use it in different platforms:
For Windows download the client from the official OpenVPN download page. Make sure to choose the correct version corresponding to your Windows(XP, Vista, 7 or later) and its architecture (32bit or 64bit).
Once you download the software install it like any other software. It’s safe to leave all options to their default values during the installation. After that obtain the OpenVPN config file. For each location you should be able to download a different file with the .ovpn extension. This is a regular text file which you can open with any text editor such as Notepad and observe the following important parameters:
- auth-user-pass – the authentication mechanism includes an user and password which you must have in order to connect.
- remote example.org 443 – this is the fully qualified domain name (FQDN) of the remote server (example.org) and the destination port (443). 443 is the standard https port which is usually allowed even in strict corporate and government firewalls. Thus if your OpenVPN provider offers the service on such a standard port, like VPNTunnel.com does, you should be able to connect from almost anywhere.
- certificate – the certificate needed to establish the secure connection with the remote server. This certificate is found inside the tags tags.
Once you have the needed .ovpn configuration file the easiest way to connect to the remote server is by clicking the right mouse button on the file and choosing “Start OpenVPN on this config file” option. Then a new prompt window will appear and you will be asked for your username and password. If your logins are correct you will be connected to the OpenVPN server and you can start browsing anonymously and safely.
This is how easy it is to establish an OpenVPN connection in Windows. In Linux and Mac the process is similar. You need again the OpenVPN client installed. For Linux the client can be found in most popular distribution repositories so the installation can be done with the native installer. For example, in Debian / Ubuntu you can install it with the command apt-get install openvpn. In Mac you need a third party software such as Tunnelblick.
After the installation you should be able to connect from a Shell terminal and using the OpenVPN binary in combination with the config file without any arguments. For example: /usr/sbin/openvpn VPNTunnel.ovpn. You will be asked for the user / password to complete the process of connecting to the remote OpenVPN server.
This is how simple and straight forward it is to use OpenVPN and protect your identity and privacy. Just don’t forget the importance of choosing a trusted OpenVPN provider, such as VPNTunnel.com, because the technology itself is not enough to protect you without the proper settings.
Top Five VPN Advantages And Benefits
VPN is a technology which creates a virtual private network to which end users are connected via an encrypted channel.
VPN is popular both among home and corporate users. Its popularity is due to the fact that it brings unmatched benefits in an interconnected world full of challenges to information security and privacy.
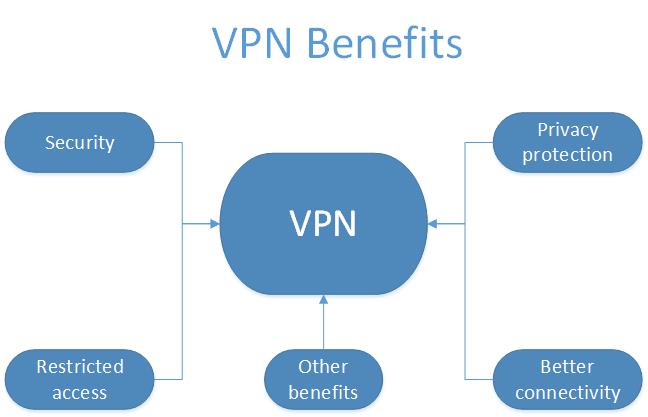
VPN has unique advantages from which the top ones are improved security, privacy protection, access to restricted resources and better connectivity.
Security
Security is one of the biggest challengers in today’s interconnected world. As soon as your PC and mobile phone are connected to the Internet, you are being targeted by unlimited number of malicious programs, viruses, hackers and other unknown new threats appearing every day. Not only this but also the information you send and received might be intercepted, read and even altered.
Local security solutions such as antivirus, firewall, etc., are not sufficient to protect you unfortunately. A separate, external solution is needed to protect the communication from you to the outside world.
That’s where VPN comes to play. VPNs secure the otherwise insecure connection between you and remote resources. VPNs should be used especially in public networks such as WiFis. In any case, as a general rule no network should be considered secure because the communication flow passes through numerous points (routers) and for an attacker is sufficient to compromise any one of these points in order to compromise the communication channel and its information flow.
However, even if the communication channel is compromised, you cannot be harmed or the harm will be minimal if you are connected to a VPN. This is because the VPN connection is encrypted and cannot be decrypted and thus read. When an attacker captures VPN traffic he will be able to see only incomprehensible characters going from you to a VPN server. Thus, the attacker is not even able to see to what remote resources you are connected (sites, chats, etc).
Privacy protection
Nowadays privacy is another serious challenge because you can be easily identified when you are online. This means that anyone from curious people and aggressive marketing company representatives to government officials can find your name, address and location with little difficulty.
As soon as you are connected online with your pc or mobile phone you are leaving traces such as your IP address and Internet service provider. This ultimately reveals essential personal information. To protect yourself from such highly undesired disclose you cannot count on any official regulations or Internet service providers.
Instead, to protect your privacy you should use VPN again. Thus, with VPN whenever you visit web sites, listen to radio, chat, etc. you will be identified with the VPN provider, i.e. his IP address, location etc. Essentially, your own IP address and personal details will remain hidden.
Using VPN for privacy protection is more than just recommended because of the frequent abuses with personal information. Furthermore, VPN is absolutely a must for any political activist or other people who have reasons to avoid disclosing their identity.
Even though there are other solutions such as web proxies to protect your identity they are not as efficient as the VPN technology. Proxies, for example, usually send information about the original IP of the client which makes them useless in regards to privacy protection.
Access to restricted resources
Sometimes service providers such as online radios, TVs, etc restrict access only to clients within certain geographical areas or Internet service providers. Other times company policies prevent employees to connect to generally available sites or resources such as Facebook. Such not always reasonable restrictions
leave you with no option but to use VPN.
VPNs have multiple points of presence in different geographic regions. The fact that you are identified only with the VPN provider allows you to circumvent any geographical restrictions.
VPNs are especially popular in countries such as China where access to sites / resources is heavily restricted. In such countries you can access anything online as long as you are connected to a VPN.
VPNs also work the other way around in access restrictions. You or your organization may wish to limit the access to certain private resources such as file shares only to a certain network segment. This is essential from security point of view because authentication is rarely enough to protect the security of sensitive information.
Here again VPNs can be used and you can allow only the VPN network to connect to such private sensitive resources.
Better connectivity
Sometimes your Internet routes may not be optimal or your bandwidth may be limited especially towards International online resources. This leads to poor web experience and slow browsing especially for certain resources which are distant from your physical location.
In such cases you can connect to a local VPN point of presence which further routes your traffic. This will allow you to have a bandwidth to distant destinations similar to the bandwidth available between you and your local VPN server.
Such better connectivity can be observed especially in users whose ISPs differentiate local (usually country-wide) resources and international such. These providers will enforce bandwidth limits on access to International resources and you can avoid these resources only by using VPN.
Other benefits
VPNs have also other benefits depending on the VPN service provider you are using. For example, some VPN service providers allow their users to share more easily and faster information between themselves, play games and perform any other activity as if they are within a local area network (LAN).
Another benefit may include port forwarding. This means that if you have a resource, e.g. web server, IP camera, etc, you wish to share to the world or access remotely you may use the VPN for this purpose. This is especially useful if your resource is located inside a local network and has an internal IP address. In such cases this resource can be configured to connect to the VPN and thus receive an external IP at which it can be accessed.
Once you find any of the above benefits attractive you have two choices. Either install a VPN sever by yourself or subscribe to a VPN service provider. Most benefits, especially the ones about privacy protection, require the use of proven VPN service providers. This in addition to the affordable prices of VPNs makes it not worth to go through all the bother to set up your own VPN server even if you have the technical knowledge.
If you haven’t chosen a VPN provider yet then check VPNTunnel. Its protection is flawless and the prices are worth the excellent service on which you can rely.
Are VPNs Safe And Trustworthy?
VPNs are virtual private networks which protect your online privacy and secure the information you send and receive. Many people wonder how safe and trustworthy VPNs are indeed.
Read this article to understand better what VPNs are, what is important for their security and to what extent you can trust them.
What are VPNs and how they protect you
It’s important that you first grasp the VPN basics in order to estimate how reliable VPNs are. First, VPNs create a private network between you (your pc or mobile smart phone) and a remote VPN server (gateway). The networks are virtual because your physical location does not matter and could be geographically far away from the gateway.
In order VPNs to work they rely upon the usual Internet connectivity and create a virtual network over it, hence the name – virtual private network. Once inside this virtual network your location and network information is hidden for the outside world when you access external resources.
Second, data encryption is used to ensure the security of the transmitted information between you and the gateway, thus preventing eavesdropping and spying over your traffic. This is especially important when you are connected to public and unsafe networks such as WiFis or monitored corporate networks.
Data encryption
Now that you know how VPNs work you should understand its key and most vulnerable components . The first and possibly the most important one is encryption.
As a general rule, no encryption (even combination of encryption algorithms) is perfectly safe. However, the time it takes for someone to decrypt your data is of essence. Strong encryption requires years to be decrypted even with powerful computers. This time lag will usually makes the information of little use.
Imagine a hacker getting finally your credit card information after 5 years when the credit card has already expired anyway. This, in addition to the huge processing resources it will require, makes usually decrypting quite unattractive to the average hacker.
However, it’s a different story when it comes to state interests and governments with serious resources come to play. There are supercomputers which decrypt information much faster and instead of years it may take weeks or even less for any information to be decrypted. Furthermore, conspiracy theories tell that some popular encryption algorithms have backdoors which may allow a certain government access to your data in no time at all.
Personal information protection
VPNs hide most of the traces which you usually leave when you are connected to Internet. When you browse web sites or chat your IP address is easily seen but with VPNs only the IP address of the gateway VPN is visible. This VPN gateway IP does not disclose any personal info about you.
Here comes the question is it possible for someone to trace you through the VPN. Most commercial VPN service providers claim that they keep no logs to indicate their clients activity. This means that it shouldn’t be possible for just anyone, including interested government representatives, to force your VPN provider to divulge information about you because this information is simply not there.
In fact the privacy protection is taken very seriously by all VPN service providers because this is the essence of their service and even a single failure may ruin their business. However, every company first and foremost is obliged to comply with the law. Thus, you should consider that your privacy is protected to the extent allowed by law and in cases of serious crimes and terrorism any company is obliged to cooperate with the law enforcement representatives.
On a side note, if you decide to manage your own VPN server instead of using a commercial provider, it is usually much easier for interested parties to trace who runs the VPN service and thus track you. That’s why it’s recommended to use a commercial VPN service even if you have the technical knowledge to create and configure one yourself.
VPNs as part of a complete security solution
VPNs are important but you should be aware that they are only one part in the security / privacy protection chain. Security begins from the device you use (personal computer, smart phone) and ends with the sites, chats, etc. you use. As with every chain, it is as strong (secure) as its weakest link is.
This means that your security and privacy can be compromised even if you use the most secure VPN but you neglect to install a reliable antivirus locally for example. No VPN can protect you from local keyloggers or other spyware.
Furthermore, don’t forget the last link of the chain, i.e. where your information arrives. Imagine that you submit your credit card information to a compromised web site. VPNs cannot help you in this case, unfortunately.
Even though there are some efforts to identify dangerous / malicious online resources you can never feel entirely safe. Just recall the numerous news stories about some of the biggest IT companies admitting theft of personal clients information after hacker attacks.
The verdict
VPNs are essential part of every Internet security solution and they cannot be replaced by other solutions such as antivirus programs. Thus, you can rely on VPNs as long as you follow all best security practices and chose a reliable VPN service provider.
Also, it’s important to understand that VPNs are designed with the best intentions in mind. Our online life is full of all kinds of online threats and VPNs can save a lot of troubles for the average user.
That’s why you are encouraged to use a VPN as part of your online security protection. In this connection it’s important to choose a reliable VPN provider which offers a strong data encryption along with clear terms of use which guarantee your privacy. If you haven’t chosen such a provider yet check VPNTunnel which offers great service at affordable price.
Finally, as a warning you should be aware that VPNs is not a solution which protects criminals and in fact there’s no such a solution at all. As you might have heard, even the most notorious and advanced online criminals get traced and caught in the end.
Setup
How To Set Up Your Own VPN With PPTP
Point-to-Point Tunneling Protocol (PPTP) is an implementation of the VPN technology commonly used in Microsoft products. Its main benefit is ease of use and native support in all modern Microsoft Windows operating systems.
Besides ease of use, PPTP also provides good encryption and authentication mechanisms to protect your security and privacy. The level of protection is sufficient for most common needs with varying strength depending on the specific PPTP server implementation.
Because of its ease of use and reliable protection PPTP has gained significant popularity. There are many VPN service providers which support PPTP along with other VPN technologies such as OpenVPN.
In some cases it might be feasible to set up your own PPTP server especially if you have the server resources and some technical background. Read this article to learn how you can do it.
PPTP Requirements
In order to set up you own PPTP VPN server you will have to satisfy some minimal hardware and software requirements.
On the hardware part you will need a computer / server with fast and Reliable internet connection. This computer must have either external real IP address or you should be able to forward (DNAT) outside connection to it through your router.
If you decide to rent a server located in a datacenter it’s most probably going to satisfy the first networking requirement. However, if you try to set up your own server at home this might be a challenge because not all ISPs allow such connectivity. Besides that you’ll have to invest in the hardware for your home server.
The hardware requirements (CPU, Memory) of the server may vary greatly depending on the PPTP implementation, the number of PPTP clients (users) and the bandwidth use you expect.
In this article you will learn how to set up a basic PPTP with minimal hardware resources such as one or two CPUs and 512 MB RAM. Linux will be used for the PPTP server because it requires less resources without the need to pay any license fees. In contrast, if you wish to use Microsoft server you will have to pay additional licensing fees and the hardware requirements will be higher.
Thanks to the low hardware requirements you may use almost any old PC (as long as it has 512 MB RAM). If you are going to buy a new piece of hardware especially for your PPTP server, a good choice is Raspberry Pi or CubieBoard. These systems are both very affordable and consume little power.
It may also come quite reasonable to rent a server. The monthly fees for such low requirements start from $5 per month. This, in addition to the networking requirements previously mentioned usually makes renting a server a better option.
As for the software requirements, any popular Linux distribution should suffice. This article emphasizes on how to set up PPTP server with Debian / Ubuntu based OS because it is most widely supported. With other Linux OS such as Redhat / Fedora / CentOS the process is similar.
PPTP server installation and configuration
To be able to follow the instructions below you will need some basic understanding of the Linux operating system. You should know how to install packages, edit files and start/stop a service as a privileged user (sudo or root).
In Debian / Ubuntu the needed server software is called pptp and can be found in the default repositories. Thus all you have to do is run the command apt-get install pptpd. To resolve dependencies this command will automatically install also the packages ppp and bcrelay.
To make sure that the pptp server daemon starts automatically with the server run the command update-rc.d pptpd defaults.
Next configure the IP addresses pool. You will need to configure the local IP address of the VPN server and the remote IPs which will be assigned to the PPTP clients. For this purpose open the file /etc/pptpd.conf and add lines such as these at the bottom:
localip 192.168.0.100 remoteip 192.168.0.200-220
In the above example, 192.168.0.100 is the IP address of the PPTP server and the clients will get addresses from 192.168.0.200 to 192.168.0.220.
After that create the users and the passwords for the PPTP server. Edit the file /etc/ppp/chap-secrets like this:
# Secrets for authentication using CHAP # client server secret IP addresses pptpuser1 pptpd OneS3cr3tPass * pptpuser2 pptpd AnotherS3cr3tPass *
The above is a table with four columns as follows:
client – this is the username which should be used for connecting to the PPTP server.
server – determines the kind of VPN server, pptpd in this case.
secret – the password for the respective user.
IP addresses – here you can specify which remote IP addresses are allowed to connect. If you not certain you can use asterisk to allow any.
Each user should have a separate row with all the needed values as you can see from the example above.
You will also have to configure the DNS servers which will be given to the PPTP clients. If you don’t have your own DNS servers you can use Google’s (8.8.8.8 and 8.8.4.4). Specify them in the file /etc/ppp/pptpd-options like this:
ms-dns 8.8.8.8 ms-dns 8.8.4.4
Once you have done all these changes you should restart the pptp service with the command service pptpd restart.
Finally you have to allow your PPTP clients to have external connectivity such as to various web sites and online services. For this purpose you will need an additional iptables rule to allow routing of the traffic. For this purpose run the commands:
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE iptables-save
The above will add and save a new iptables rule in your nat table to allow PPTP clients external access.
PPTP client setup
The easiest part is to configure the PPTP clients because the technology is well supported in any modern operating system.
For Windows clients you don’t need any additional software installation. You just have to follow the intuitive wizard found in Network and Sharing Center. There choose to set up a new connection or network. For more information check this PPTP client setup guide for Windows 7 or this one for Windows 8.
This article explains how easy and simple it is to set up your own PPTP VPN server. However, usually it’s better to benefit from the services of professionals who will take care of all the small details to ensure your maximum protection. If you are interested check the affordable VPN services provided by VPNTunnel.
